More compliant and better control of risks — always In Control.
IRM360 brings order to complex legislation, regulations, and frameworks.
We support organizations—from SMEs to government, healthcare, critical entities, and enterprises—in managing cybersecurity, privacy, AI, and business continuity risks, as well as in demonstrating compliance and certification.
In a single integrated platform, you can secure ISO 27001, Cbw-NIS2, GDPR, DORA, AI legislation, and 46+ other standards and frameworks.
Start with our Plug & Play management systems, such as the ISMS for information security, and expand at your own pace to full GRC control.
Immediate clarity and control over what is happening now and what is coming in the future — with a smart, scalable concept that ensures fast, optimal, and cost-efficient implementation and assurance.



Trusted by users in government, healthcare, trade and industry, business and financial services, and SMEs.

Error:
Value cannot be null. Parameter name: mediaItem : at Umbraco.Web.ImageCropperTemplateExtensions.GetCropUrl(IPublishedContent mediaItem, Nullable`1 width, Nullable`1 height, String propertyAlias, String cropAlias, Nullable`1 quality, Nullable`1 imageCropMode, Nullable`1 imageCropAnchor, Boolean preferFocalPoint, Boolean useCropDimensions, Boolean cacheBuster, String furtherOptions, Nullable`1 ratioMode, Boolean upScale) at ASP._Page_Views_Partials_Thumbnail_cshtml.Execute() in d:\wwwroot\IRM360\www\Views\Partials\Thumbnail.cshtml:line 37Error:
Value cannot be null. Parameter name: mediaItem : at Umbraco.Web.ImageCropperTemplateExtensions.GetCropUrl(IPublishedContent mediaItem, Nullable`1 width, Nullable`1 height, String propertyAlias, String cropAlias, Nullable`1 quality, Nullable`1 imageCropMode, Nullable`1 imageCropAnchor, Boolean preferFocalPoint, Boolean useCropDimensions, Boolean cacheBuster, String furtherOptions, Nullable`1 ratioMode, Boolean upScale) at ASP._Page_Views_Partials_Thumbnail_cshtml.Execute() in d:\wwwroot\IRM360\www\Views\Partials\Thumbnail.cshtml:line 37Error:
Value cannot be null. Parameter name: mediaItem : at Umbraco.Web.ImageCropperTemplateExtensions.GetCropUrl(IPublishedContent mediaItem, Nullable`1 width, Nullable`1 height, String propertyAlias, String cropAlias, Nullable`1 quality, Nullable`1 imageCropMode, Nullable`1 imageCropAnchor, Boolean preferFocalPoint, Boolean useCropDimensions, Boolean cacheBuster, String furtherOptions, Nullable`1 ratioMode, Boolean upScale) at ASP._Page_Views_Partials_Thumbnail_cshtml.Execute() in d:\wwwroot\IRM360\www\Views\Partials\Thumbnail.cshtml:line 37Error:
Value cannot be null. Parameter name: mediaItem : at Umbraco.Web.ImageCropperTemplateExtensions.GetCropUrl(IPublishedContent mediaItem, Nullable`1 width, Nullable`1 height, String propertyAlias, String cropAlias, Nullable`1 quality, Nullable`1 imageCropMode, Nullable`1 imageCropAnchor, Boolean preferFocalPoint, Boolean useCropDimensions, Boolean cacheBuster, String furtherOptions, Nullable`1 ratioMode, Boolean upScale) at ASP._Page_Views_Partials_Thumbnail_cshtml.Execute() in d:\wwwroot\IRM360\www\Views\Partials\Thumbnail.cshtml:line 37Error:
Value cannot be null. Parameter name: mediaItem : at Umbraco.Web.ImageCropperTemplateExtensions.GetCropUrl(IPublishedContent mediaItem, Nullable`1 width, Nullable`1 height, String propertyAlias, String cropAlias, Nullable`1 quality, Nullable`1 imageCropMode, Nullable`1 imageCropAnchor, Boolean preferFocalPoint, Boolean useCropDimensions, Boolean cacheBuster, String furtherOptions, Nullable`1 ratioMode, Boolean upScale) at ASP._Page_Views_Partials_Thumbnail_cshtml.Execute() in d:\wwwroot\IRM360\www\Views\Partials\Thumbnail.cshtml:line 37Error:
Value cannot be null. Parameter name: mediaItem : at Umbraco.Web.ImageCropperTemplateExtensions.GetCropUrl(IPublishedContent mediaItem, Nullable`1 width, Nullable`1 height, String propertyAlias, String cropAlias, Nullable`1 quality, Nullable`1 imageCropMode, Nullable`1 imageCropAnchor, Boolean preferFocalPoint, Boolean useCropDimensions, Boolean cacheBuster, String furtherOptions, Nullable`1 ratioMode, Boolean upScale) at ASP._Page_Views_Partials_Thumbnail_cshtml.Execute() in d:\wwwroot\IRM360\www\Views\Partials\Thumbnail.cshtml:line 37Error:
Value cannot be null. Parameter name: mediaItem : at Umbraco.Web.ImageCropperTemplateExtensions.GetCropUrl(IPublishedContent mediaItem, Nullable`1 width, Nullable`1 height, String propertyAlias, String cropAlias, Nullable`1 quality, Nullable`1 imageCropMode, Nullable`1 imageCropAnchor, Boolean preferFocalPoint, Boolean useCropDimensions, Boolean cacheBuster, String furtherOptions, Nullable`1 ratioMode, Boolean upScale) at ASP._Page_Views_Partials_Thumbnail_cshtml.Execute() in d:\wwwroot\IRM360\www\Views\Partials\Thumbnail.cshtml:line 37Error:
Value cannot be null. Parameter name: mediaItem : at Umbraco.Web.ImageCropperTemplateExtensions.GetCropUrl(IPublishedContent mediaItem, Nullable`1 width, Nullable`1 height, String propertyAlias, String cropAlias, Nullable`1 quality, Nullable`1 imageCropMode, Nullable`1 imageCropAnchor, Boolean preferFocalPoint, Boolean useCropDimensions, Boolean cacheBuster, String furtherOptions, Nullable`1 ratioMode, Boolean upScale) at ASP._Page_Views_Partials_Thumbnail_cshtml.Execute() in d:\wwwroot\IRM360\www\Views\Partials\Thumbnail.cshtml:line 37Error:
Value cannot be null. Parameter name: mediaItem : at Umbraco.Web.ImageCropperTemplateExtensions.GetCropUrl(IPublishedContent mediaItem, Nullable`1 width, Nullable`1 height, String propertyAlias, String cropAlias, Nullable`1 quality, Nullable`1 imageCropMode, Nullable`1 imageCropAnchor, Boolean preferFocalPoint, Boolean useCropDimensions, Boolean cacheBuster, String furtherOptions, Nullable`1 ratioMode, Boolean upScale) at ASP._Page_Views_Partials_Thumbnail_cshtml.Execute() in d:\wwwroot\IRM360\www\Views\Partials\Thumbnail.cshtml:line 37Error:
Value cannot be null. Parameter name: mediaItem : at Umbraco.Web.ImageCropperTemplateExtensions.GetCropUrl(IPublishedContent mediaItem, Nullable`1 width, Nullable`1 height, String propertyAlias, String cropAlias, Nullable`1 quality, Nullable`1 imageCropMode, Nullable`1 imageCropAnchor, Boolean preferFocalPoint, Boolean useCropDimensions, Boolean cacheBuster, String furtherOptions, Nullable`1 ratioMode, Boolean upScale) at ASP._Page_Views_Partials_Thumbnail_cshtml.Execute() in d:\wwwroot\IRM360\www\Views\Partials\Thumbnail.cshtml:line 37Error:
Value cannot be null. Parameter name: mediaItem : at Umbraco.Web.ImageCropperTemplateExtensions.GetCropUrl(IPublishedContent mediaItem, Nullable`1 width, Nullable`1 height, String propertyAlias, String cropAlias, Nullable`1 quality, Nullable`1 imageCropMode, Nullable`1 imageCropAnchor, Boolean preferFocalPoint, Boolean useCropDimensions, Boolean cacheBuster, String furtherOptions, Nullable`1 ratioMode, Boolean upScale) at ASP._Page_Views_Partials_Thumbnail_cshtml.Execute() in d:\wwwroot\IRM360\www\Views\Partials\Thumbnail.cshtml:line 37IRM360 is a platform for Integrated Risk Management, with European roots and international reach.
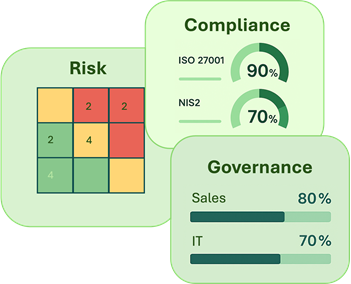
Where many tools reduce compliance to superficial audit logic and separate integrations, IRM360 helps organizations to actually organize risks and make them manageable—for responsible staff officers, management, the board, and supervisors.
The IRM360 CyberManager ensures this with a smart Plan-Do-Check-Act task system that makes Excel redundant, collects evidence in a structured manner, and provides continuously updated insight. This creates an overview and control of risks, control measures, and compliance per standard, domain, line, and organization.
No checkboxes, but responsible decisions — with insight and control through simplicity.
Immediately deployable and fully scalable
IRM360 offers a flexible and quick-to-adopt alternative to traditional GRC models with our Integrated Risk Management solution — ideal in a world where standards and legislation are constantly changing.
You start at the level that suits your organization — small or broad — and easily scale up by adding our Plug & Play management systems and standards to the CyberManager Core (Foundation, Advanced, or Pro). This way, the solution grows with your objectives — without large upfront investments, without complex implementations, without starting over, and always with fast results.
ISMS PIMS CSMS BCMS AIMS QMS FRMS

Roel Brand
Information Security Officer, Gemeente Deurne

For the ISMS of the municipality of Deurne, I use CyberManager very actively. It helps me to implement the BIO measures thoroughly and across the board, and it makes the final ENSIA self-assessment efficient.
Sebastiaan Jacobs
Brandmasters

Very happy with this software; it helps us with our corporate governance, quality control, and IT (security)!
Arend Feenstra
PMO, mydatafactory

The IRM360 CyberManager software is central to our ISO 27001 certification processes. The software is logically structured and configurable according to standard requirements. With the help of the PIMS module, we can also perform clear and organized DPIAs. We can wholeheartedly recommend IRM360's services to other potential users.
Gert-Jan
CEO, FysioTape

With the help of the IRM360 Management Systems, we were able to get our privacy management up and running very quickly to comply with the GDPR.
Jor
Information Security Officer, Exite ICT

The CyberManager from IRM360 is an ISMS tool that fits our needs well and supports us in achieving and maintaining ISO 27001 certification. As a customer, you can provide a lot of input for new functionality; very nice!
Maurice Sanders
Corporate Security & Privacy Officer, insign.it

With the help of CyberManager, we manage our ISO 27001, NEN 7510, ISO 9001 certifications, the ISAE 3402 standard, and GDPR requirements. CyberManager guides the activities related to the PDCA cycle and assigns actions to the responsible individuals in the organization. A significant improvement compared to working on 'paper' or in Excel.
Nathalie Verkade
Compliance Officer, TechoneNL

The CyberManager ISMS from IRM360 has supported us in achieving ISO 27001 and NEN 7510 certifications for several of our subsidiaries.
Robin Carter
V Net Solutions, Sydney

We achieved ISO 27701 certification with the help of CyberManager. The software provided excellent support for consolidating and integrating ISO 27001 and ISO 27701 into a single platform, and our auditor was impressed with the support and implementation provided within CyberManager.
Michiel
Privacy Officer, PROUD NERDS

The CyberManager from IRM360 provides excellent templates to get started immediately and gain control over the entire PDCA cycle. We achieved ISO 27001 certification in one go. Without CyberManager, that would never have been possible. We also manage all other aspects related to our Information Security & Privacy using CyberManager.
Erwin Lensink
Directeur, DataVisual

With the templates available in IRM360 CyberManager, we were able to quickly and independently get our ISO 27001 management system operational and achieved our ISO 27001 certification.
Tonnie Puijk
IT Manager, Beheerd.nl

We had been working on ISO 27001 certification for some time but kept getting stuck because we didn’t have a framework/system for an ISMS. The P/ISMS CyberManager helped us gain more control over these processes. The framework and templates also forced us to think about things you might otherwise forget, and we achieved our certification within a few months.
Erik Reek
ISO, NControl & Mosadex E-Health

We were the first management organization in the healthcare sector to achieve our NEN7510-2017 certification with the help of the IRM360 Management System, the CyberManager from IRM360.
Monique Verdouw
Director/Founder EventTouch

We were able to easily convert our existing ISMS and ISO 27001 certification information and evidence into the P/ISMS CyberManager. No more separate documents and complex Excel files. This saves time, money, and hassle around periodic tasks such as risk analyses, audits, and reports.
Plug & Play Compliance
More than 46 standards & frameworks available
A smart link between controls and standards ensures that the compliance status of each control is automatically propagated to all connected standards, giving you instant insight into compliance per standard.
The result: less duplicate work and maximum consistency. Achieving compliance with multiple standards at the same time has never been easier.
Our promise

Fast and easy implementation

One control — covering multiple standards

Insight into the organization, business lines, and internal audit

Optimal control of risks and data breaches

Cost-efficient licenses and management